浙江省赛决赛2025_Re
总结
线下赛暴露了自己很多问题,继续沉淀
Reverse
你是我的天命人吗
类smc,跟进加载后的情况
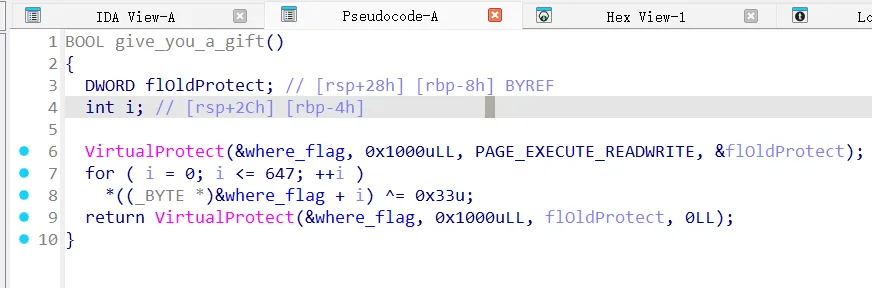
1 | |
androidtest
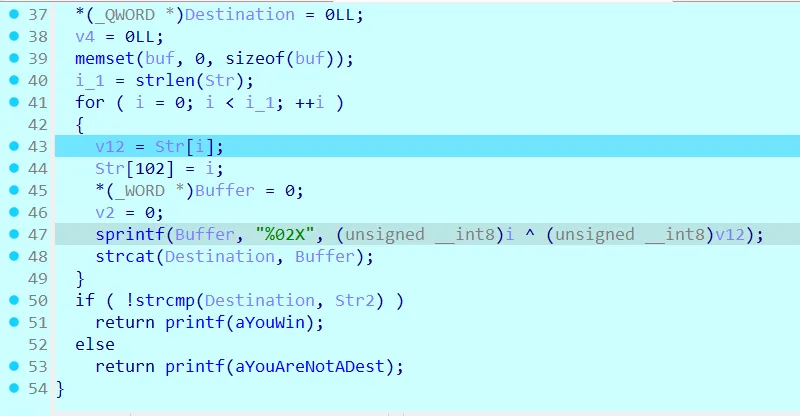
xor+base32
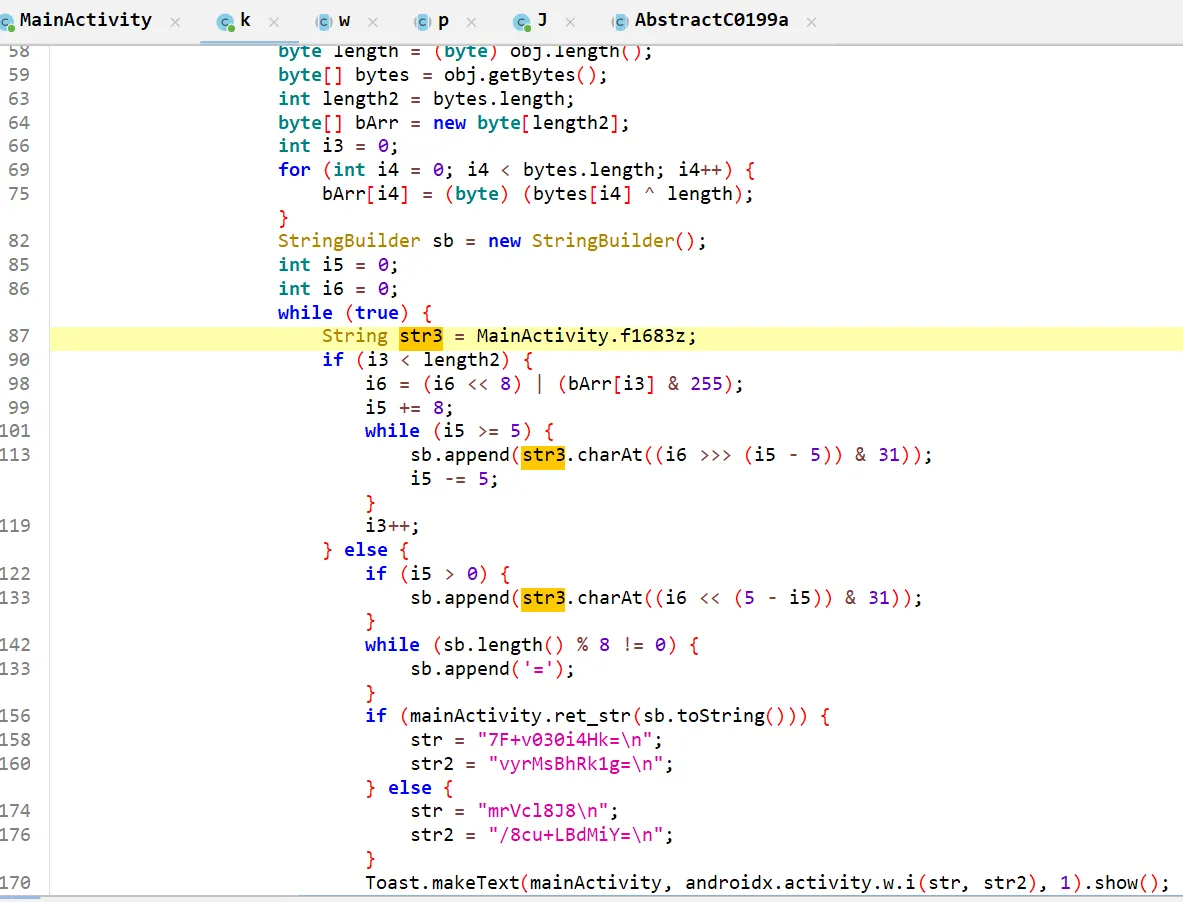
base32,一直以为是变表,其实没变,AbstractC0199a.a混淆处未知,比赛时忘用jeb分析
1 | |
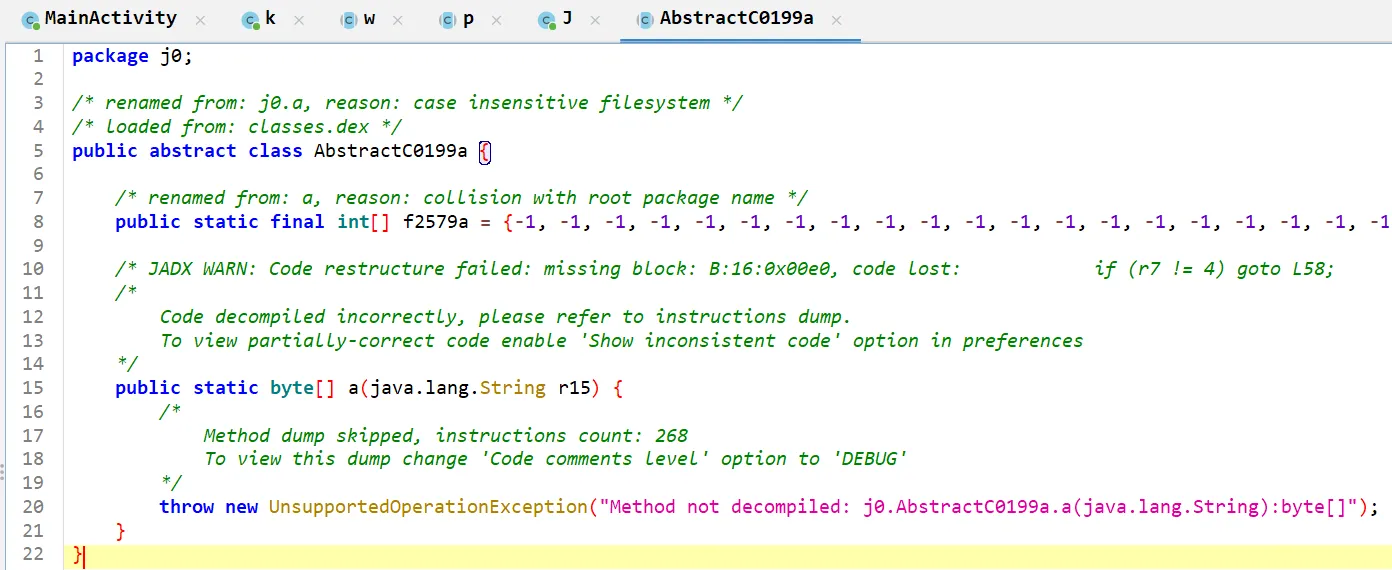
换jeb清晰很多
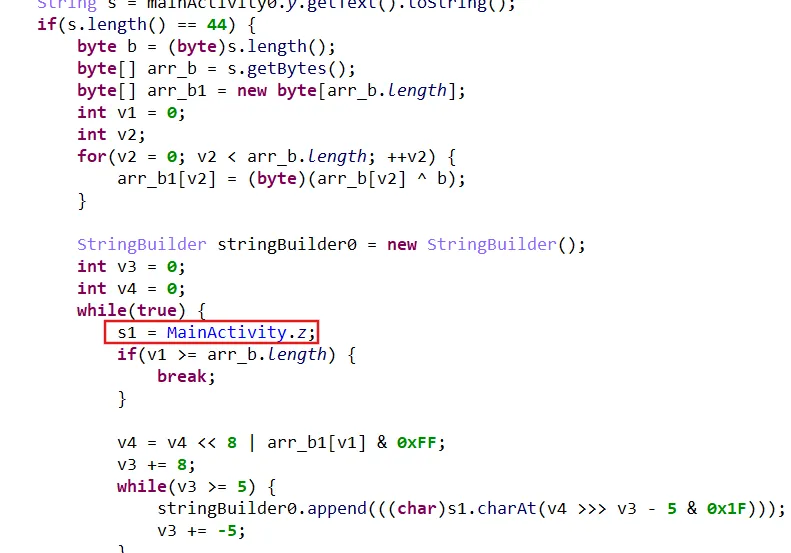
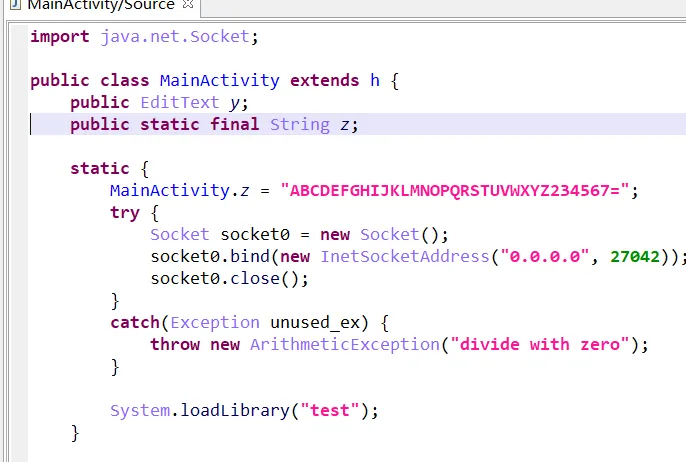
so层enc
1 | |
解密
1 | |
Warning! Warning!(复现)
vm,tracelog还原opcode
trace xor
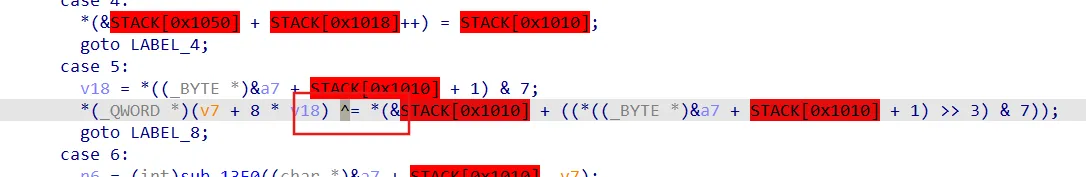
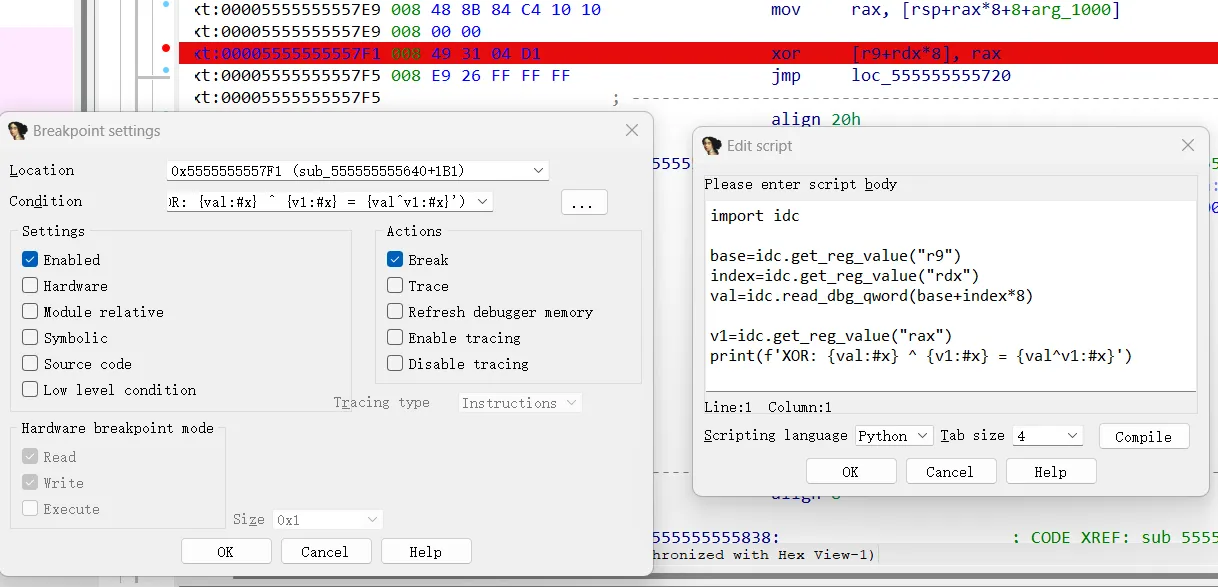
1 | |
trace cmp
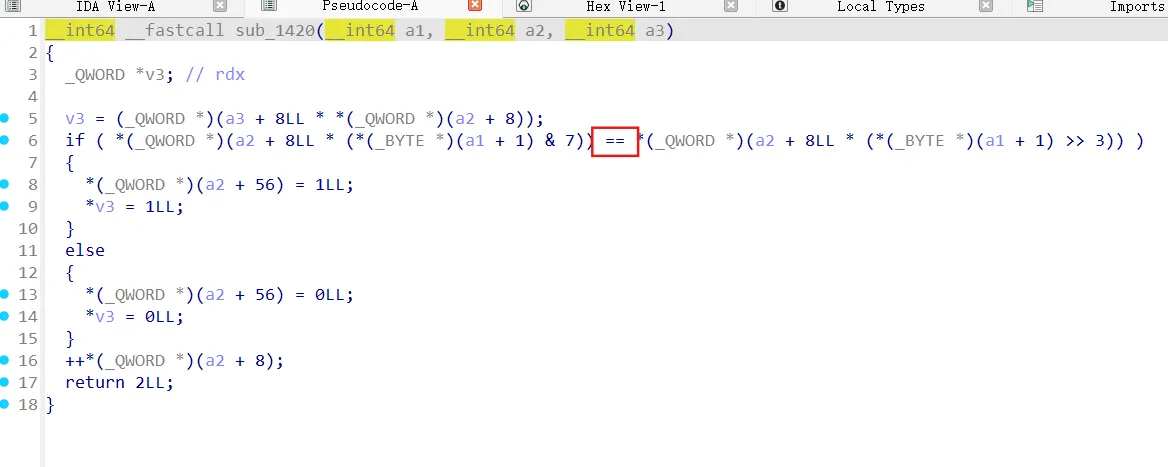
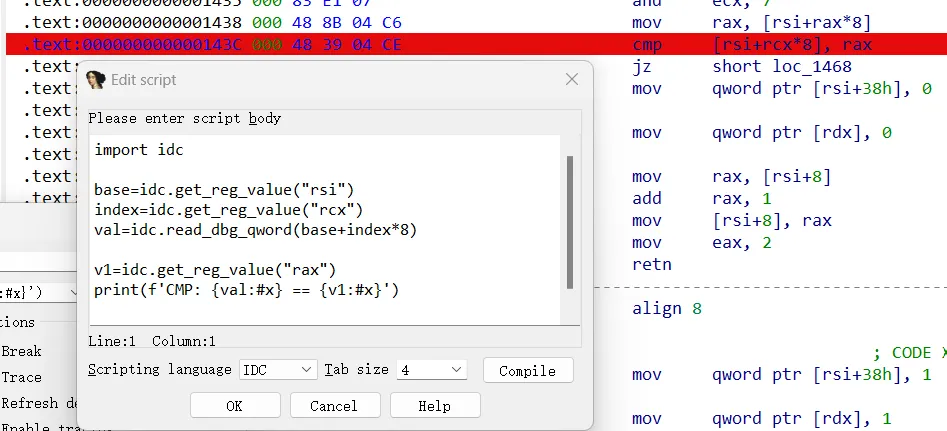
1 | |
命令行输入检测,长度为0x40,按长度位异或,再是0x100=256,联想rc4,还是凭感觉吧,将中间结果与密钥流异或
1 | |
异或回去
1 | |
信创安全
鸿蒙逆向,hap解压为一个项目
工具:abc-decompiler
matrix+xor+rc4+base64
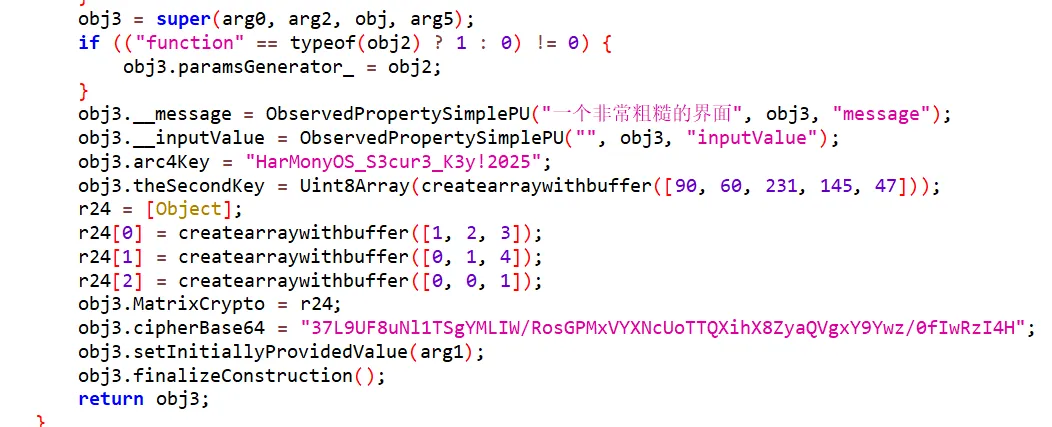
1 | |
解密
1 | |
浙江省赛决赛2025_Re
https://alenirving.github.io/2025/11/18/浙江省赛决赛2025_Re/