强网拟态just复现
前言
比赛没打,复现了下,好评,加深了对il2cpp以及dumper工具的理解
Just
refer:
基于apk的unity,il2cpp
dumper失败,metadata.dat和libil2cpp.so有加密
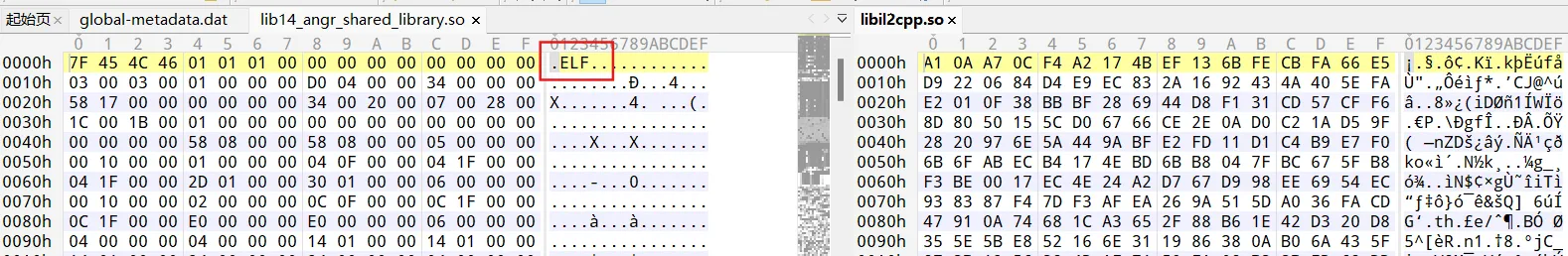
0x400h
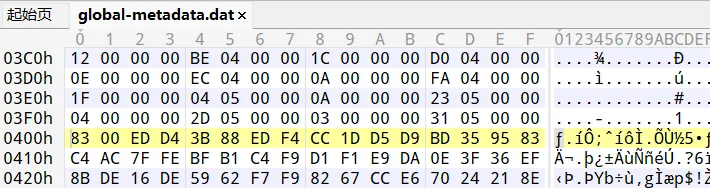
ida分析libjust.so
sub_8A0C为so解密函数,rc4 && xor
1 | |
本地报错:cannot continue after an internal error, sorry,但arm下能看到相关字样
sub_B6CC android_dlopen_ext
1 | |
dobbyHook框架实现hook
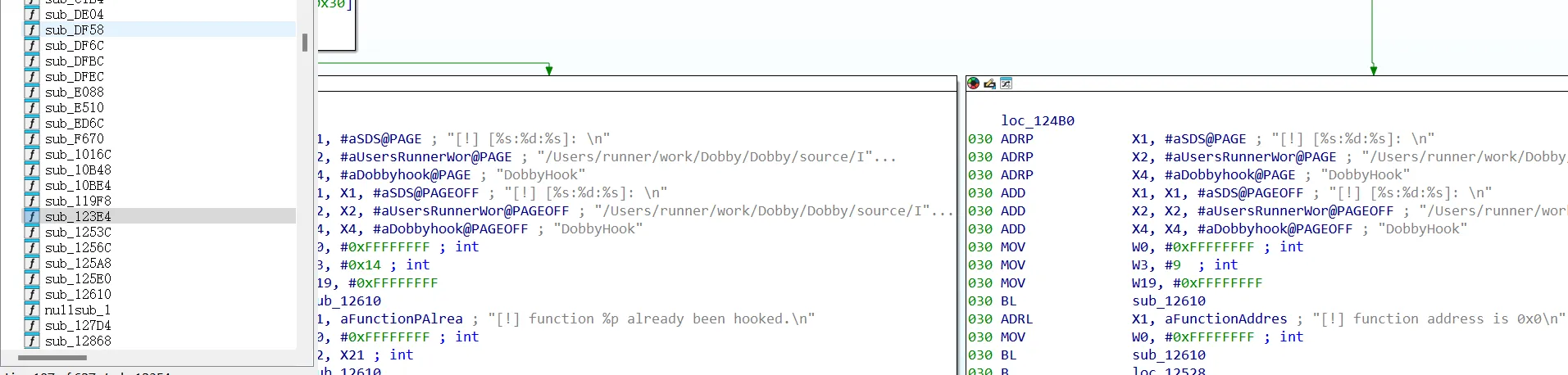
1 | |
eg.
1 | |
so解密跟进分析mat解密
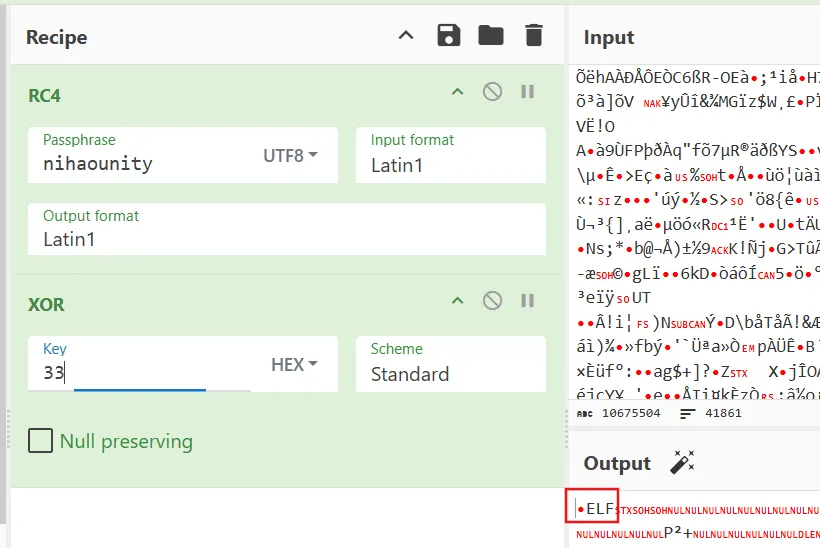
字符串查找定位到加载global-metadata.dat的部分
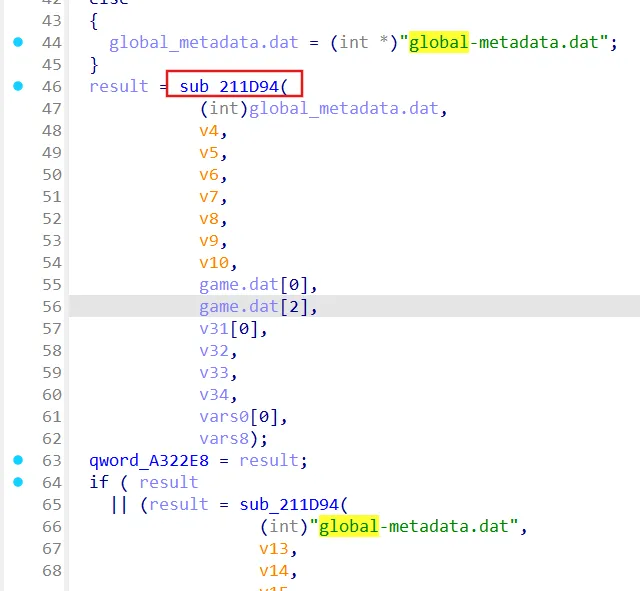
内部原本为mmap函数
1 | |
1 | |
关注返回值v26所在函数
1 | |
1 | |
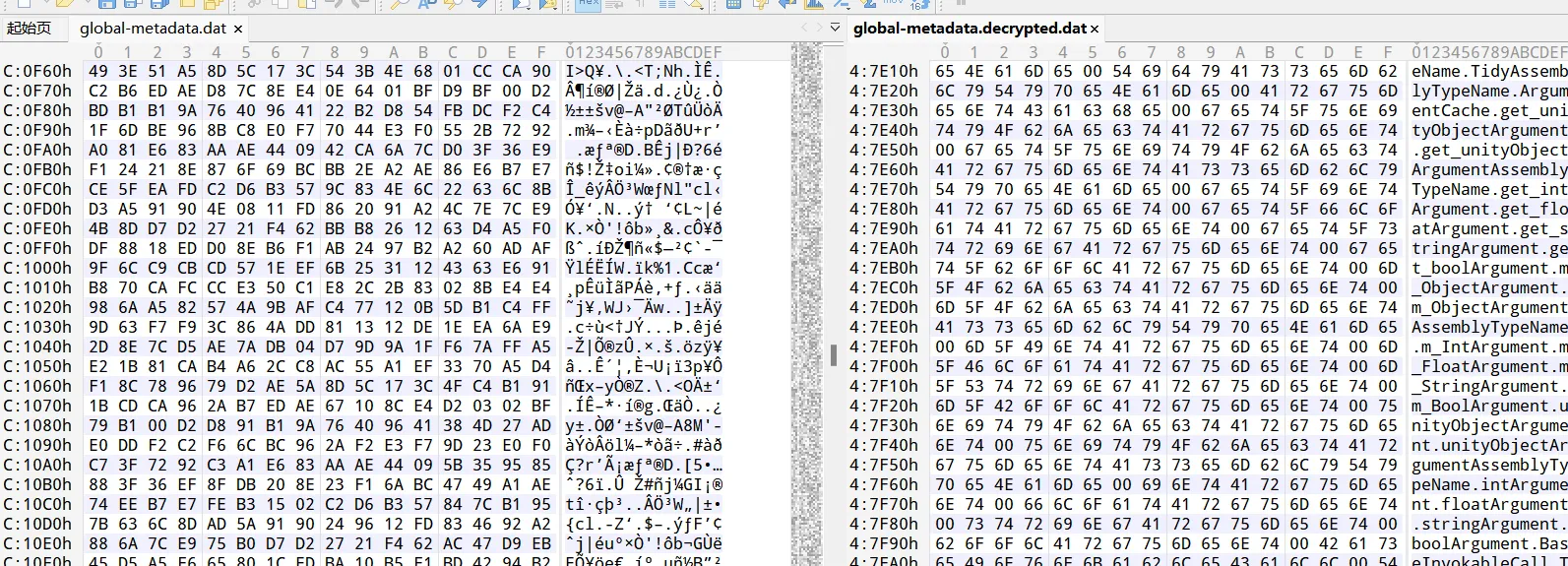
il2cppdumper
1 | |
Il2CppDumper 只能恢复函数签名和元数据,不能恢复实际逻辑,去so下分析
这里一开始忘记导入ida恢复符号了,感谢大洋参师傅
可以frida dump,笔者模拟器一加无法运行,静态分析
frida脚本
1 | |
0x41C330
1 | |
0x419F2C
1 | |
一处tea,一处tea+xor,这个^是真的丁真啊我去,八百行瞄这玩意
找key和密文
看cctor构造函数
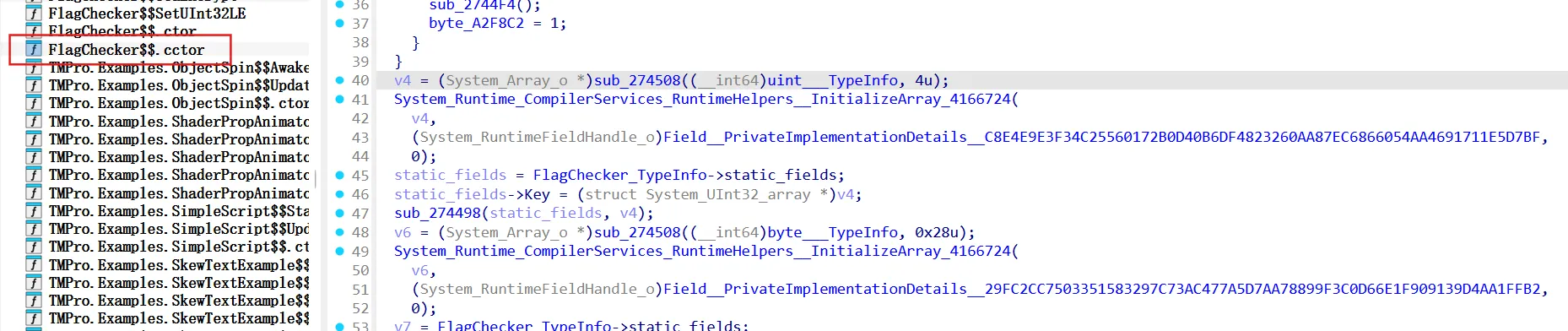
对应hash
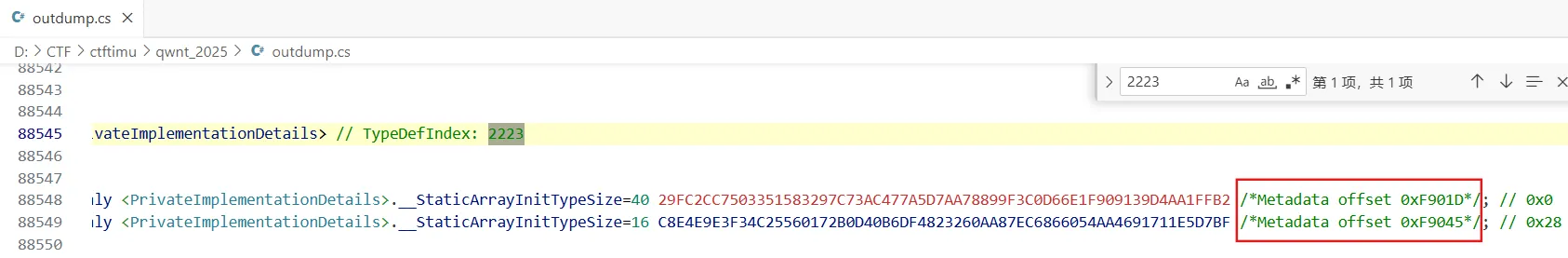
解密
1 | |
强网拟态just复现
https://alenirving.github.io/2025/11/09/强网拟态just复现/