前言 尝试学习angr在混淆下的应用,示例eg.exe源于封装好的现成solutions下
项目:https://github.com/jakespringer/angr_ctf
又是一个re✌:https://github.com/ZERO-A-ONE/AngrCTF_FITM/tree/master
ubuntu配置32位环境:
1 2 3 4 sudo dpkg --add-architecture i386sudo apt install libc6:i386 libstdc++6:i386sudo apt-get updatesudo apt install libncurses5-dev lib32z1
去除烦人警告
1 2 import logging'angr.storage.memory_mixins.default_filler_mixin' ).setLevel(logging.CRITICAL)
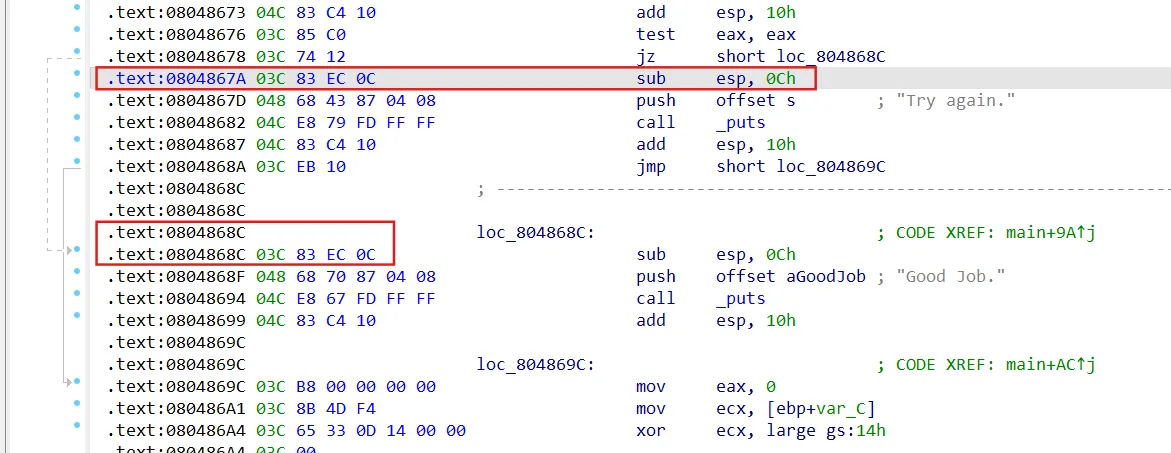
00_find
1 2 3 4 5 6 7 8 9 10 11 12 13 import angr'00_angr_find' )0x804868C ,avoid=0x804867A )if simulation.found:0 ]print (solution_state.posix.dumps(0 ).decode())else :assert 'fail'
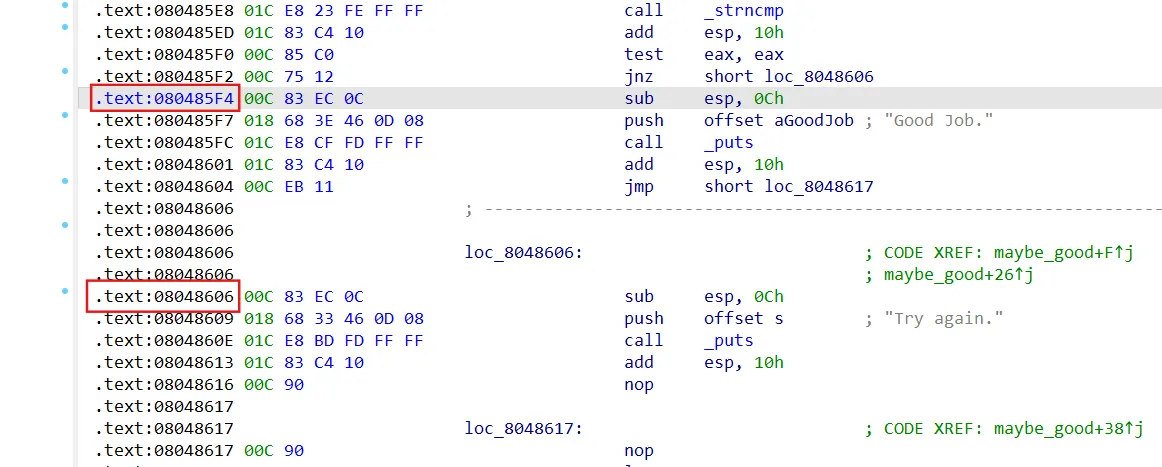
01_avoid
find地址附近即可,avoid改为avoid_me函数地址,绕过减少solver时间
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 import angr'./01_angr_avoid' )0x80485F4 0x80485BF if simgr.found:0 ]print (solution_state.posix.dumps(0 ).decode())
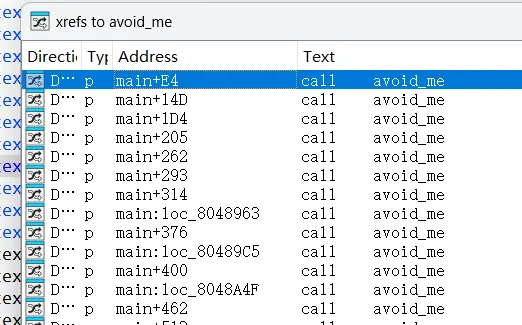
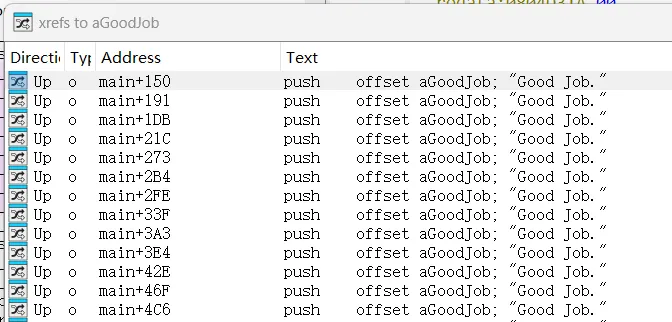
02_def_addr 上一关调用大量avoid_me,此关则是两个对应输出语句被大量调用,采用下述写法处理没有具体地址情况
eg.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 import angrdef success (state ):1 )return b'Good Job' in outputdef failure (state ):1 )return b'Try again' in output'./02_angr_find_condition' )if simulation.found:0 ]print (state.posix.dumps(0 ).decode())else :assert False
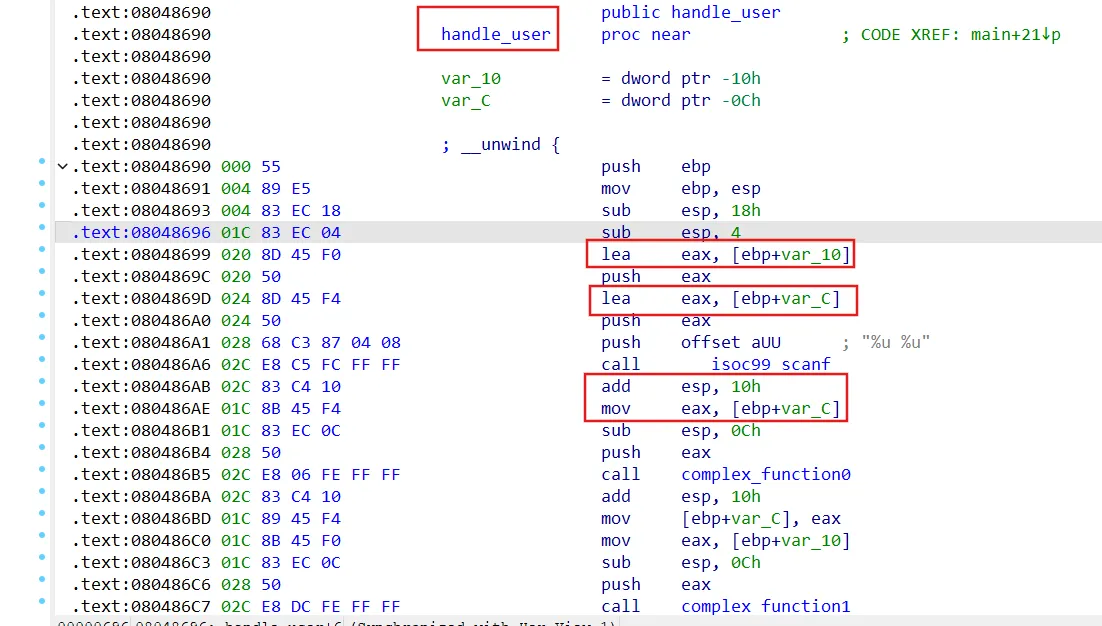
03_register angr不支持多个scanf输入,scanf调用结束后指定angr注入地址
1 2 3 4 5 6 7 8 9 10 int get_user_input () int v1; int v2; 4 ]; 1 ] = __readgsdword(0x14u );"%x %x %x" , &v1, &v2, v3);return v1;
此关新增将符号值注入寄存器
补充:
方法
说明
entry_state()
从程序入口开始
blank_state(addr==…)
从指定地址开始,完全空白
full_init_state()
执行到 main
call_state(addr,arg11,arg2,…)
专门用于调用某个函数,自动设置参数和返回地址
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 int __cdecl main (int argc, const char **argv, const char **envp) int v5; int v6; int v7; int v8; printf ("Enter the password: " );if ( v5 || v6 || v8 )puts ("Try again." );else puts ("Good Job." );return 0 ;
wk.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 import angrimport claripy'./03_angr_symbolic_registers' )0x080488C7 32 32 32 'hoge0' ,hoge0_size)'hoge1' ,hoge1_size)'hoge2' ,hoge2_size)0x0804892A ,avoid=0x08048918 )if simulation.found:0 ]eval (hoge0)eval (hoge1)eval (hoge2)'' .join(map ('{:08x}' .format ,[a0,a1,a2]))print (a)else :assert False
04_stack 此关跳过scanf的目的地在一个函数内部,需重新构建一个栈环境,像上一关直接将返回值返回给对应寄存器,栈的影响不重要,此关数据仍在栈中,需要构建模拟scanf后的情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 import angrimport claripy'./04_angr_symbolic_stack' )0x080486AE 'hoge0' ,32 )'hoge1' ,32 )8 def success (state ):1 )return 'Good Job.' .encode() in outputdef fail (state ):1 )return 'Try again.' .encode() in outputif simulation.found:0 ]eval (hoge0)eval (hoge1)' ' .join(map (str ,[a0,a1]))print (s)else :print ('fail' )
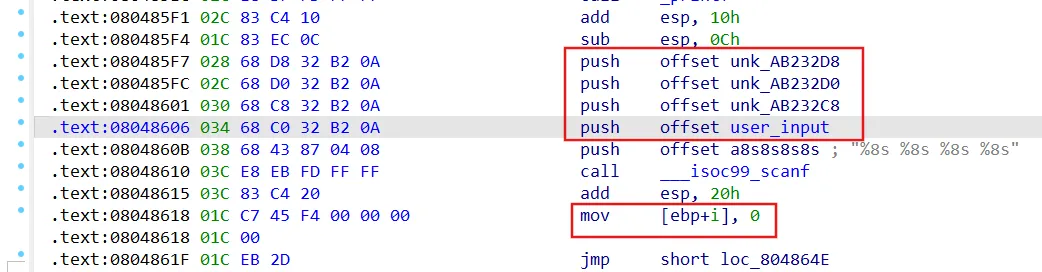
05_memory_store 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 int __cdecl main(int argc, const char **argv, const char **envp)int i; // [esp+Ch] [ebp-Ch]0 , 0x21u);"Enter the password: " );"%8s %8s %8s %8s" , user_input, &unk_AB232C8, &unk_AB232D0, &unk_AB232D8);for ( i = 0 ; i <= 31 ; ++i )0xAB232C0 ) = complex_function(*(char *)(i + 0xAB232C0 ), i);if ( !strncmp(user_input, "OSIWHBXIFOQVSBZBISILSCLBIAXSEWUT" , 0x20u) )"Good Job." );else "Try again." );return 0 ;
wk.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 import angrimport claripy'./05_angr_symbolic_memory' )0x08048618 'a' ,8 *8 ) 'b' ,64 )'c' ,64 )'d' ,64 )0xab232c0 0xab232c8 0xab232d0 0xab232d8 def success (state ):1 )return 'Good Job.' .encode() in outputdef fail (state ):1 )return 'Try again.' .encode() in outputif simulation.found:0 ]eval (a,cast_to=bytes ).decode()eval (b,cast_to=bytes ).decode()eval (c,cast_to=bytes ).decode()eval (d,cast_to=bytes ).decode()' ' .join([q,w,e,r])print (s)else :print ('fail' )
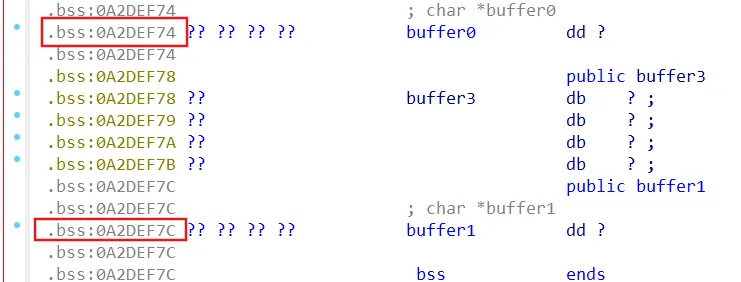
06_malloc_memory 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 int __cdecl main (int argc, const char **argv, const char **envp) int i; char *)malloc (9u );char *)malloc (9u );memset (buffer0, 0 , 9u );memset (buffer1, 0 , 9u );printf ("Enter the password: " );"%8s %8s" , buffer0, buffer1);for ( i = 0 ; i <= 7 ; ++i )32 );if ( !strncmp (buffer0, "OSIWHBXI" , 8u ) && !strncmp (buffer1, "FOQVSBZB" , 8u ) )puts ("Good Job." );else puts ("Try again." );free (buffer0);free (buffer1);return 0 ;
改用地址指针,此关模拟heap堆
补充:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 程序中调用了 malloc(9),
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 import angrimport claripy'./06_angr_symbolic_dynamic_memory' )0x080486AF 'a' ,8 *8 ) 'b' ,64 )0x1111111 0xa2def74 4 )0x1111121 0xa2def7c 4 )def success (state ):1 )return 'Good Job.' .encode() in outputdef fail (state ):1 )return 'Try again.' .encode() in outputif simulation.found:0 ]eval (a,cast_to=bytes ).decode()eval (b,cast_to=bytes ).decode()' ' .join([q,w])print (s)else :print ('fail' )
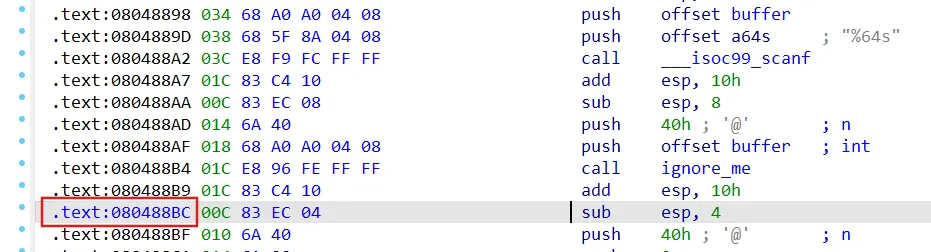
07_file 模拟文件读取
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 int __cdecl __noreturn main (int argc, const char **argv, const char **envp) int v3; int v4; int v5; int v6; int v7; int v8; int i; memset (buffer, 0 , sizeof (buffer));printf ("Enter the password: " );"%64s" , buffer, v3, v4, v5, v6, v7, v8);0x40u );memset (buffer, 0 , sizeof (buffer));"FOQVSBZB.txt" , "rb" );1u , 0x40u , fp);"FOQVSBZB.txt" );for ( i = 0 ; i <= 7 ; ++i )0x804A0A0 ) = complex_function(*(char *)(i + 134520992 ), i);if ( strcmp (buffer, "OSIWHBXI" ) )puts ("Try again." );exit (1 );puts ("Good Job." );exit (0 );
wk.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 import angrimport claripy'./07_angr_symbolic_file' )0x080488BC 'FOQVSBZB.txt' 8 'password' , symbolic_file_size_bytes * 8 )def success (state ):1 )return 'Good Job.' .encode() in outputdef fail (state ):1 )return 'Try again.' .encode() in outputif simulation.found:0 ]eval (password,cast_to=bytes ).decode()print (s)else :print ('fail' )
补充:
概念 类型 含义 是否符号化 典型用途
BVSclaripy.BVS(name, size)符号变量(Symbolic Variable)
是
表示未知输入(如密码、密钥)
BVVclaripy.BVV(value, size)具体值(Concrete Value)
否
表示已知常量(如 “hello”)
dumps(0)state.posix.dumps(0)获取程序从 stdin 读入的数据
可能包含符号,但输出 concrete
查看输入内容、调试
solver.eval(...)state.solver.eval(expr)求解符号表达式 的具体值
输入是符号,输出是 concrete
得到密码、密钥等答案
08_constrain 处理字符串
符号执行16轮相当于2^16次,手动给出指定地址绕过字符串处理
跳过字符串处理
blank设置具体参数
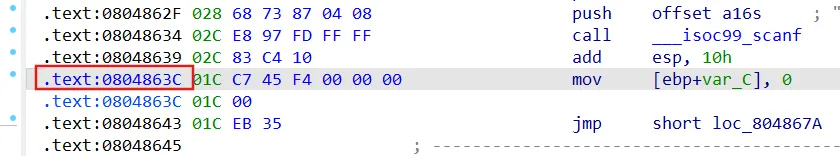
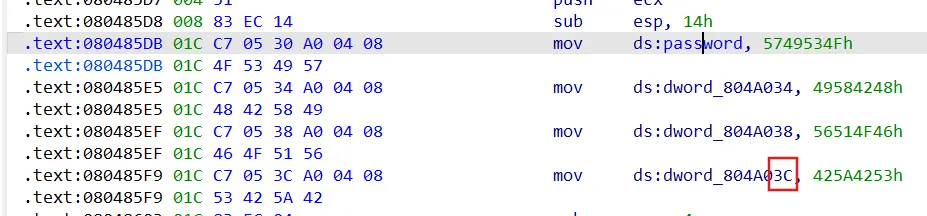
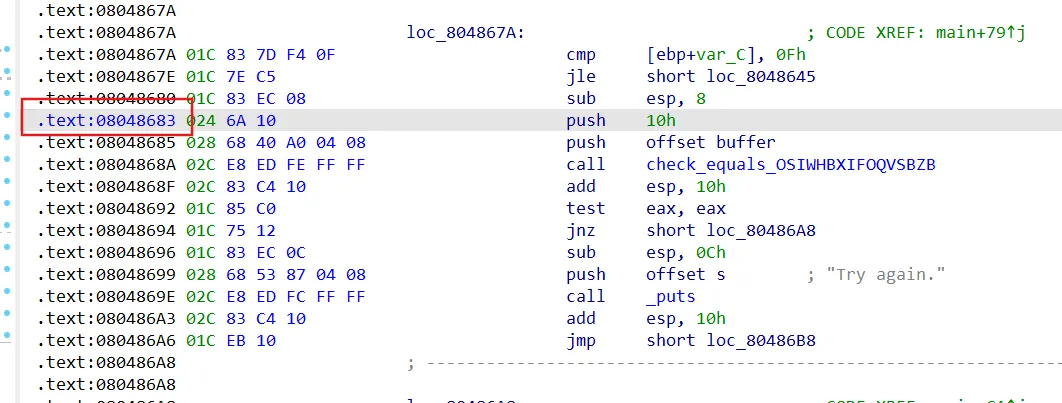
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 import angrimport claripy'./08_angr_constraints' )0x0804863C 'passwd' ,8 *16 )0x804a040 0x8048683 if simulation.found:0 ]0x804a040 16 'OSIWHBXIFOQVSBZB' .encode()eval (passwd,cast_to=bytes ).decode()print (solution)else :raise Exception('No solution found' )
entry自行填充
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 import angrimport claripy'./08_angr_constraints' )0x8048683 if simulation.found:0 ]0x804a040 16 'OSIWHBXIFOQVSBZB' .encode()print (solution.posix.dumps(0 ).decode())else :print ('fail' )
09_hook angr的hook方法
主逻辑如下,两次输入以及校验,angr hook函数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 int __cdecl main (int argc, const char **argv, const char **envp) int i; int j; "OSIWHBXIFOQVSBZB" , 16 );memset (buffer, 0 , 0x11u );printf ("Enter the password: " );"%16s" , buffer);for ( i = 0 ; i <= 15 ; ++i )0x804A044 ) = complex_function(*(char *)(i + 0x804A044 ), 18 - i);16 );for ( j = 0 ; j <= 15 ; ++j )0x804A034 ) = complex_function(*(char *)(j + 0x804A034 ), j + 9 );"%16s" , buffer);strncmp (buffer, password, 0x10u );if ( equals )puts ("Good Job." );else puts ("Try again." );return 0 ;
关于此处字符串比较不用绕过的解释:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 int strncmp (const char *s1, const char *s2, size_t n) {for (size_t i = 0 ; i < n; i++) {if (s1[i] != s2[i]) {return s1[i] - s2[i];if (s1[i] == '\0' ) { return 0 ;return 0 ;
wk.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 import angrimport claripy'./09_angr_hooks' )0x080486CA 5 @project.hook(check_equal_addr,length=instruction_len ) def skip_check_equal (state ):0x804A044 len =16 len )'OSIWHBXIFOQVSBZB' .encode()1 ,32 ),0 ,32 )def success (state ):1 )return 'Good Job.' .encode() in outputdef fail (state ):1 )return 'Try again.' .encode() in outputif simulation.found:0 ]0 ).decode()print (solution)else :print ('fail' )
python装饰器
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 check_equal_addr=0x080486CA 5 @project.hook(check_equal_addr,length=instruction_len ) def skip_check_equal (state ):0x804A044 len =16 len )'OSIWHBXIFOQVSBZB' .encode()1 ,32 ),0 ,32 )def skip_check_equal (state ):0x804A044 len = 16 len )'OSIWHBXIFOQVSBZB' .encode()1 , 32 ),0 , 32 )
10_simprocedures 多轮加密,利用simprocedures简化处理,替换调用函数,原理不变:
1.hook 函数本身的地址
2.memory.load(regs.esp + xx)读取栈中函数
3.设eax返回值
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 int __cdecl main (int argc, const char **argv, const char **envp) int i; 17 ]; unsigned int v6; 0x14u );memcpy (&password, "OSIWHBXIFOQVSBZB" , 0x10u );memset (s, 0 , sizeof (s));printf ("Enter the password: " );"%16s" , s);for ( i = 0 ; i <= 15 ; ++i )char )s[i], 18 - i);if ( check_equals_OSIWHBXIFOQVSBZB((int )s, 0x10u ) )puts ("Good Job." );else puts ("Try again." );return 0 ;
wk.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 import angrimport claripy'./10_angr_simprocedures' )class replacement_check_equal (angr.SimProcedure):def run (self,to_check,len ):len self .state.memory.load(input_addr,input_len)'OSIWHBXIFOQVSBZB' .encode()return claripy.If(1 ,32 ),0 ,32 )'check_equals_OSIWHBXIFOQVSBZB' def success (state ):1 )return 'Good Job.' .encode() in outputdef fail (state ):1 )return 'Try again.' .encode() in outputif simulation.found:0 ]0 ).decode()print (solution)else :print ('fail' )
11_sim_scanf simprocedures处理多个输入
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 .text:08048711 04 C 83 EC 04 sub esp, 4 08048714 050 68 F8 8 A 06 08 push offset buffer108048719 054 68 0 C 3 A 06 08 push offset buffer00804871 E 058 68 83 FD 04 08 push offset aUU ; "%u %u" 08048723 05 C E8 28 FD FF FF call ___isoc99_scanf08048728 05 C 83 C4 10 add esp, 10 h11 _angr_sim_scanf | grep scanf #-d disassemble11 _angr_sim_scanf: 文件格式 elf32-i38608048450 <__isoc99_scanf@plt>:8048723 : e8 28 fd ff ff call 8048450 <__isoc99_scanf@plt>804878 e: e8 bd fc ff ff call 8048450 <__isoc99_scanf@plt>8048802 : e8 49 fc ff ff call 8048450 <__isoc99_scanf@plt>804886 d: e8 de fb ff ff call 8048450 <__isoc99_scanf@plt>80488 ee: e8 5 d fb ff ff call 8048450 <__isoc99_scanf@plt>8048959 : e8 f2 fa ff ff call 8048450 <__isoc99_scanf@plt>
wk.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 import angrimport claripy'./11_angr_sim_scanf' )class replacement_scanf (angr.SimProcedure):def run (self,format_string,string1_addr,string2_addr ):'string1' ,32 )'string2' ,32 )self .state.memory.store(string1_addr,string1,endness=project.arch.memory_endness)self .state.memory.store(string2_addr,string2,endness=project.arch.memory_endness)self .state.globals ['solution1' ]=string1self .state.globals ['solution2' ]=string2'__isoc99_scanf' def success (state ):1 )return 'Good Job.' .encode() in outputdef fail (state ):1 )return 'Try again.' .encode() in outputif simulation.found:0 ]globals ['solution1' ]globals ['solution2' ]f'{solution_state.solver.eval (s1)} {solution_state.solver.eval (s2)} ' print (solution)else :print ('fail' )
12_veritesting 主要引入veritesting概念
“Enhancing Symbolic Execution with Veritesting” (Avgerinos et al., ICSE 2014)
核心思想:结合动态符号执行(concolic execution)与静态路径展开(static path enumeration) ,在遇到复杂控制流(如循环、深层嵌套条件)时,自动“展开”部分代码区域,生成多条路径,从而避免过早陷入某一条路径而错过其他可能的解。
eg.
1 2 3 4 5 6 7 8 9 10 11 simgr = project.factory.simgr(initial_state, veritesting=True )True ,'enable_function_inlining' : False ,'max_iterations' : 10 ,'loop_unrolling_limit' : 5
wk. 自己这里本地没跑通,github上跑通的为2020年样例,等佬研究
附官方的
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 import angrimport sysdef main (argv ):1 ]True )def is_successful (state ):return 'Good Job.' .encode() in stdout_output def should_abort (state ):return 'Try again.' .encode() in stdout_output if simulation.found:0 ]print (solution_state.posix.dumps(sys.stdin.fileno()).decode())else :raise Exception('Could not find the solution' )if __name__ == '__main__' :
13_static_binary 未打包库函数的静态elf,手动加载
留意_libc_start_main函数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 void __usercall __noreturn start (int stack_end_@<eax>, void (*rtld_fini)(void )@<edx>) int argc; int stack_end__1; char *ubp_av_; int (*)(int , char **, char **))main,void (*)(void ))_libc_csu_init,void (*)(void ))_libc_csu_fini,080487F 0 void __usercall __noreturn start (int stack_end_@<eax>, void (*rtld_fini)(void )@<edx>)
wk.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 import angr'./13_angr_static_binary' )0x804fab0 , angr.SIM_PROCEDURES['libc' ]['printf' ]())0x804fb10 , angr.SIM_PROCEDURES['libc' ]['scanf' ]())0x80503f0 , angr.SIM_PROCEDURES['libc' ]['puts' ]())0x8048d60 , angr.SIM_PROCEDURES['glibc' ]['__libc_start_main' ]())def success (state ):1 )return 'Good Job.' .encode() in output def fail (state ):1 )return 'Try again.' .encode() in output if simulation.found:0 ]print (solution_state.posix.dumps(0 ).decode())else :raise Exception('Could not find the solution' )
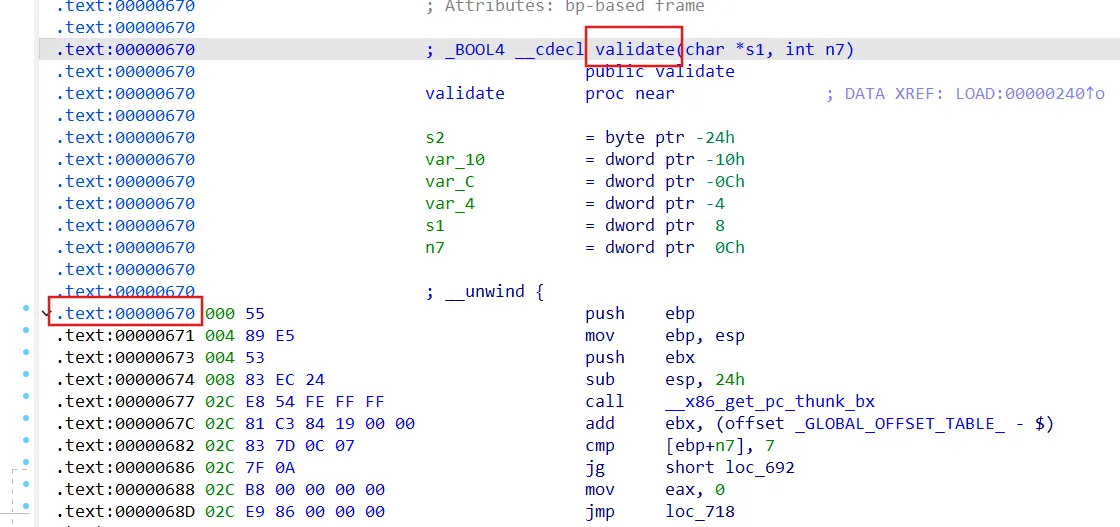
14_so 学起来跟frida思路很想啊,包括后面的地址偏移
so文件下的validate函数
1 2 3 (base) ma5k@ma5k-Ubuntu24:~/angr_ctf-master/solutions/14_angr_shared_library$ checksec --file=14_angr_shared_library
no pie,基址不变
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 import angrimport claripy"./lib14_angr_shared_library.so" 0x4000000 'main_opts' : {'custom_base_addr' : base0x3000000 , 32 )0x670 8 , 32 ),'password' , 8 *8 )0x71c if simulation.found:0 ]0 )eval (password, cast_to=bytes ).decode()print (solution)else :raise Exception('Could not find the solution' )
pre-binary 选项:
如果你想要对一个特定的二进制对象设置一些选项,CLE也能满足你的需求在加载二进制文件时可以设置特定的参数,使用 main_opts 和 lib_opts 参数进行设置。
backend - 指定 backendbase_addr - 指定基址entry_point - 指定入口点arch - 指定架构
示例如下:
1 2 >>> angr.Project('examples/fauxware/fauxware', main_opts={'backend': 'blob', 'arch': 'i386'}, lib_opts={'libc.so.6': {'backend': 'elf'}})
参数main_opts和lib_opts接收一个以python字典形式存储的选项组。main_opts接收一个形如{选项名1:选项值1,选项名2:选项值2……}的字典,而lib_opts接收一个库名到形如{选项名1:选项值1,选项名2:选项值2……}的字典的映射。
lib_opts是二级字典,原因是一个二进制文件可能加载多个库,而main_opts指定的是主程序加载参数,而主程序一般只有一个,因此是一级字典。
这些选项的内容因不同的后台而异,下面是一些通用的选项:
backend —— 使用哪个后台,可以是一个对象,也可以是一个名字(字符串)
custom_base_addr —— 使用的基地址
custom_entry_point —— 使用的入口点
custom_arch —— 使用的处理器体系结构的名字
后记 后续关卡为无条件约束以及溢出类pwn利用了,不是很感兴趣,暂时学到这,完工