UCSCCTF2025
总结
emm,头一次拿一等和ak Re,但是质量仍待商榷,crypto:web=6,队内密码手进修rsa整数分解问题去了
Re
simplere
魔改ep section upx壳
1 | |
两段加密,大致是base58和xor
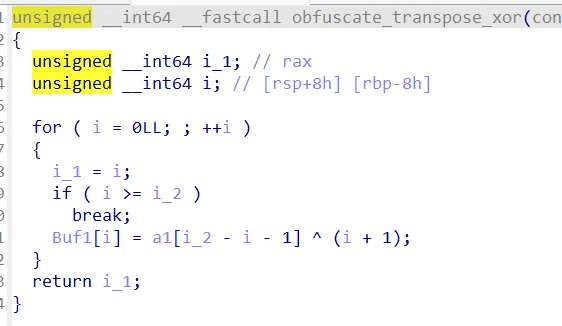
base58变表,第一次遇到,加密过程和代码值得关注,以防以后的魔改
1 | |
1 | |
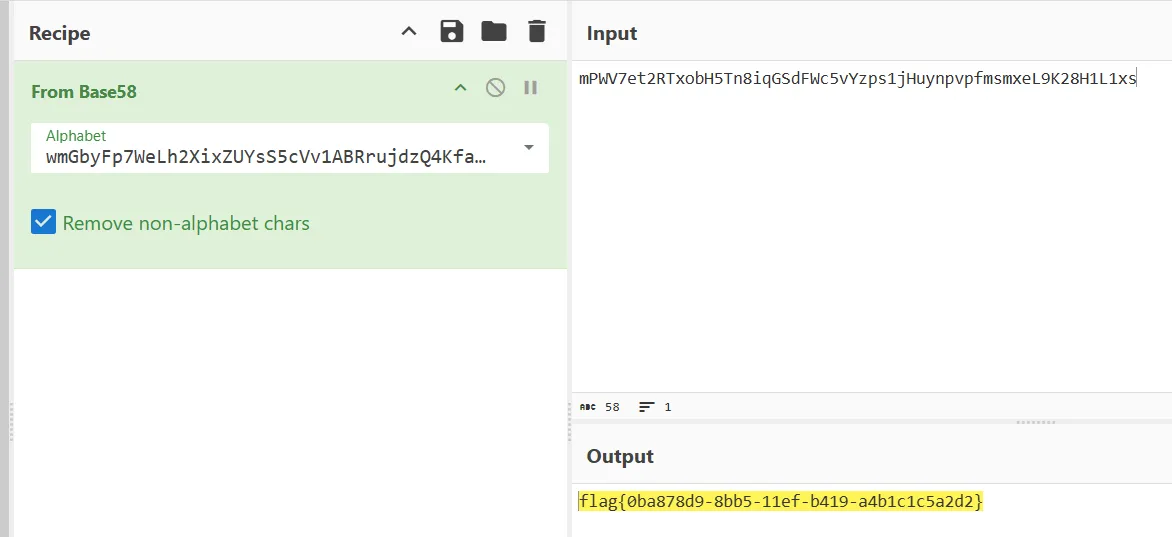
easy_re
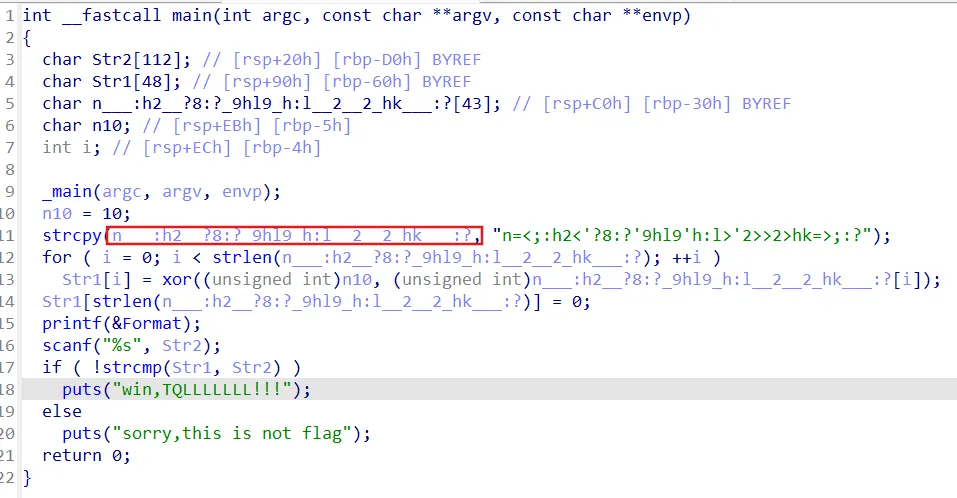
n___:h2__?8:?9hl9_h:l__2__2_hk__:?
为以防万一,先留个底
好吧,就一简单xor
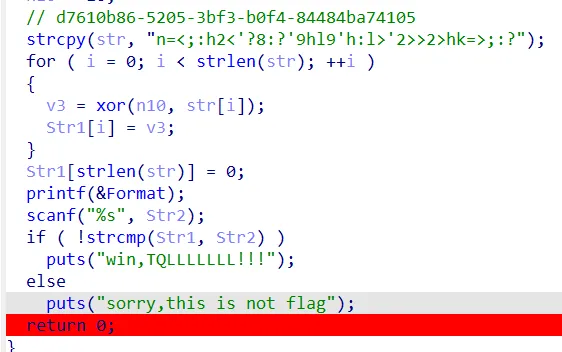
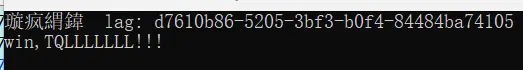
为什么flag{d7610b86-5205-3bf3-b0f4-84484ba74105}不对???
是平台的问题,出了
ez_debug
rc4解密,没有魔改,一开始想多了,顺带试了下手搓
1 | |
有错误,赛后去找
因为是对称加密,动调取数据就完了
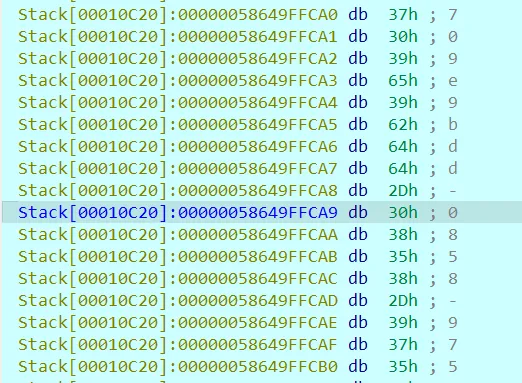
1 | |
re_ez
对输入进行判断,分析加密逻辑即可
借助ai分析了主要思路,大致如下:
对输入数据进行处理,var = (*(_BYTE *)v18 - 32) ^ 3; 不得>=4
n0x18 += qword_7FF732F40498[(char)var]; n0x18取值 +1,-1,+5,-5
1 | |
复现或者没下载的可看下述代码,一开始动调没整明白判断前的一堆函数加载具体意义,可能是rust语言特性吧
1 | |
Pwn
userlogin
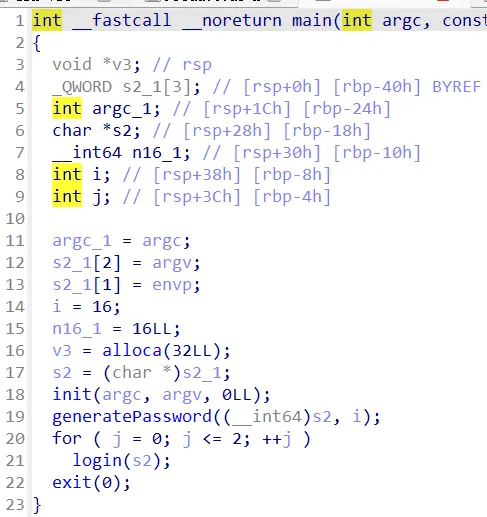
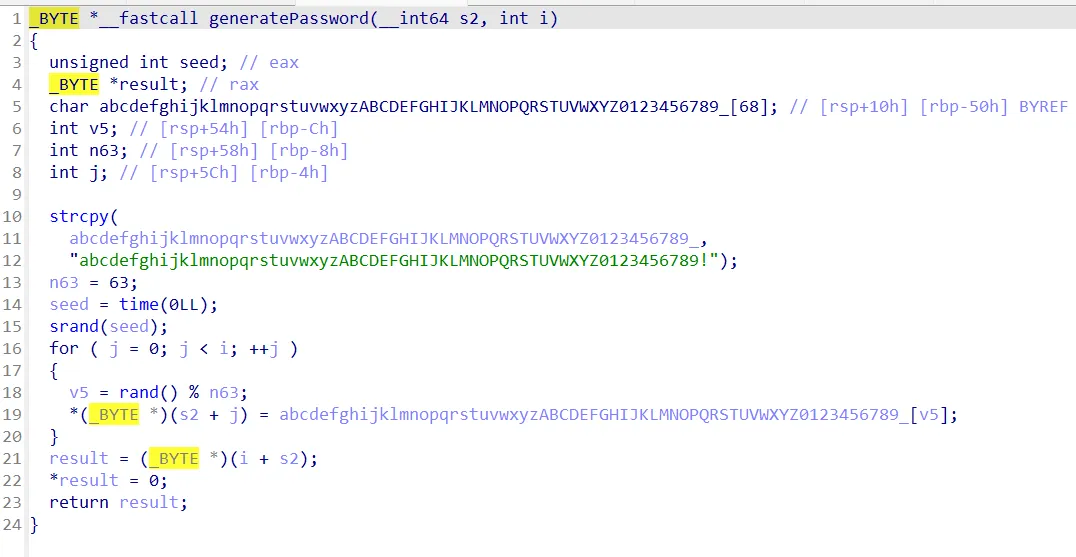
login下root()函数scanf未限制输入长度
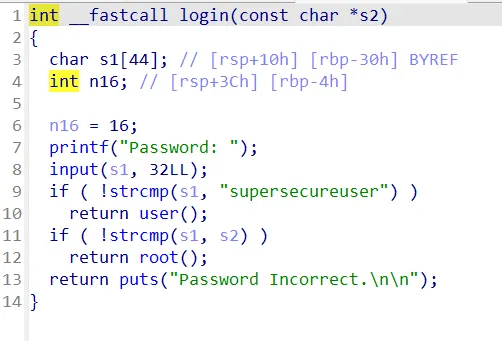
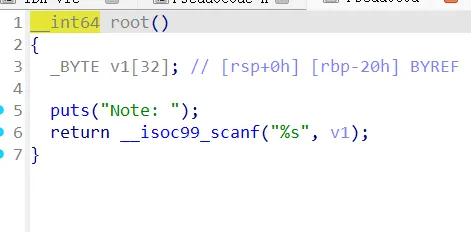
有个shell()函数
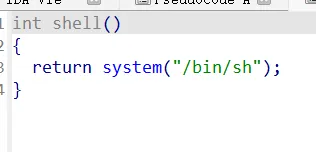
payload:
1 | |
1 | |
UCSCCTF2025
https://alenirving.github.io/2025/04/20/UCSCCTF2025/